Information security Risk management in ISO 27000
Information security Risk management in ISO 27000
Effect: Risk is about the effect, which can be a deviation from the expected—positive or negative.
Uncertainty: Risk arises from the uncertainty that can affect the achievement of objectives.
Objectives: These are the goals or desired outcomes that an organization seeks to achieve. They can exist at various levels of the organization, from strategic to operational.
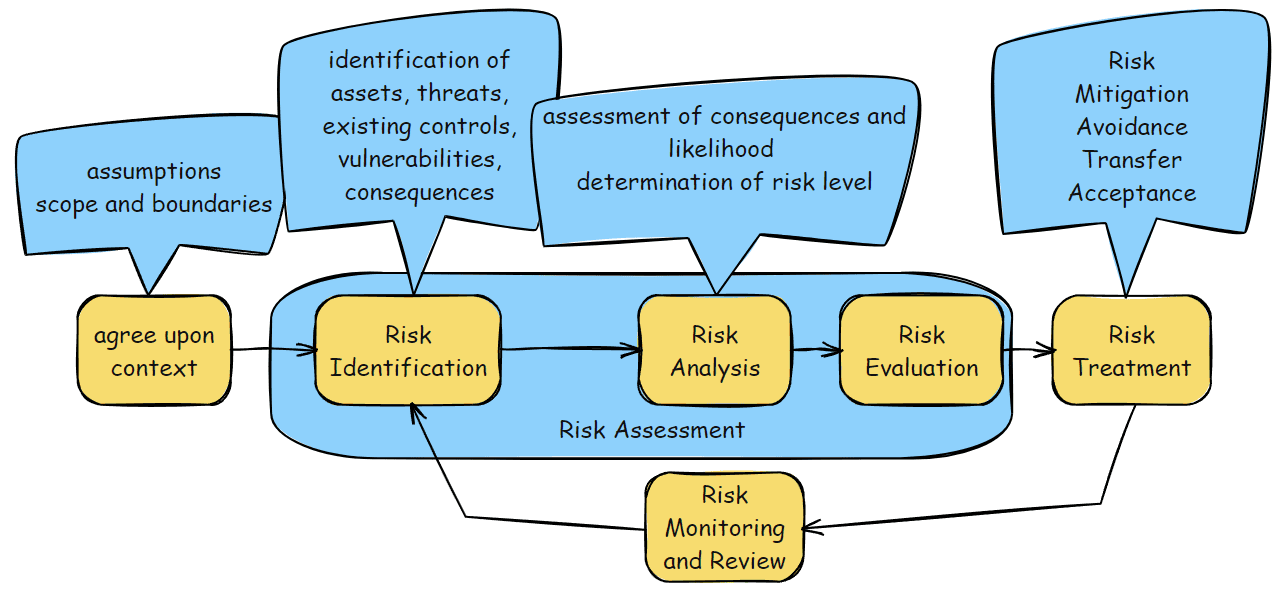
The Stages of Risk Management are:
The Stages of Risk Management are:
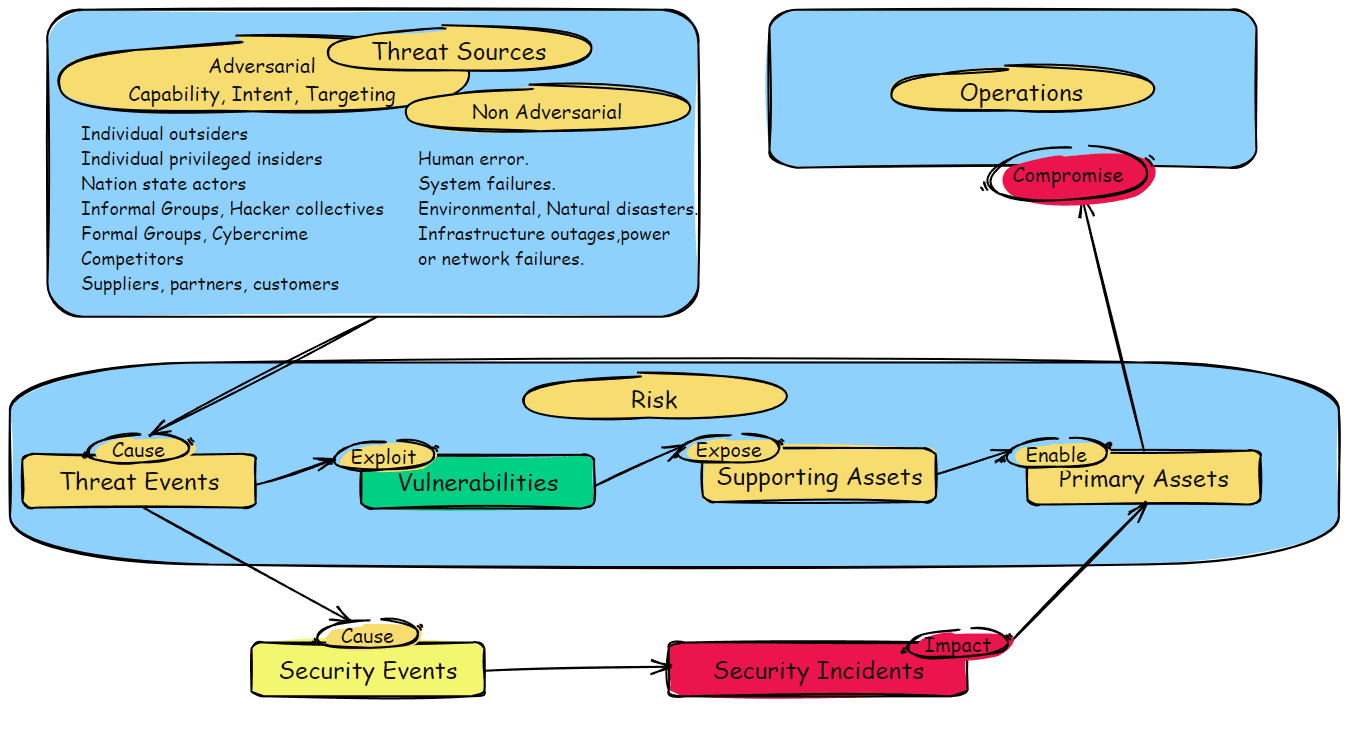
Threat Sources, Threat Events, Vulnerabilities, Security events, Security incidents:
- Hardware: Servers, computers
- Software: Applications, databases
- Network: Internet connection, firewalls
- Personnel: Employees, contractors
- Sites: Physical locations like offices or data centers
- your business data, orders, project data
- your customers data
- your customers billing data
- contact details of your customers
- patents and copyrights
- company financial data
- login details for making payments
- personal data of employees
- proprietary software - source code
- scientific research results
- schematics and internal production processes and workflows
- formulas
- data about your products or technologies (e.g. recipe, source code)
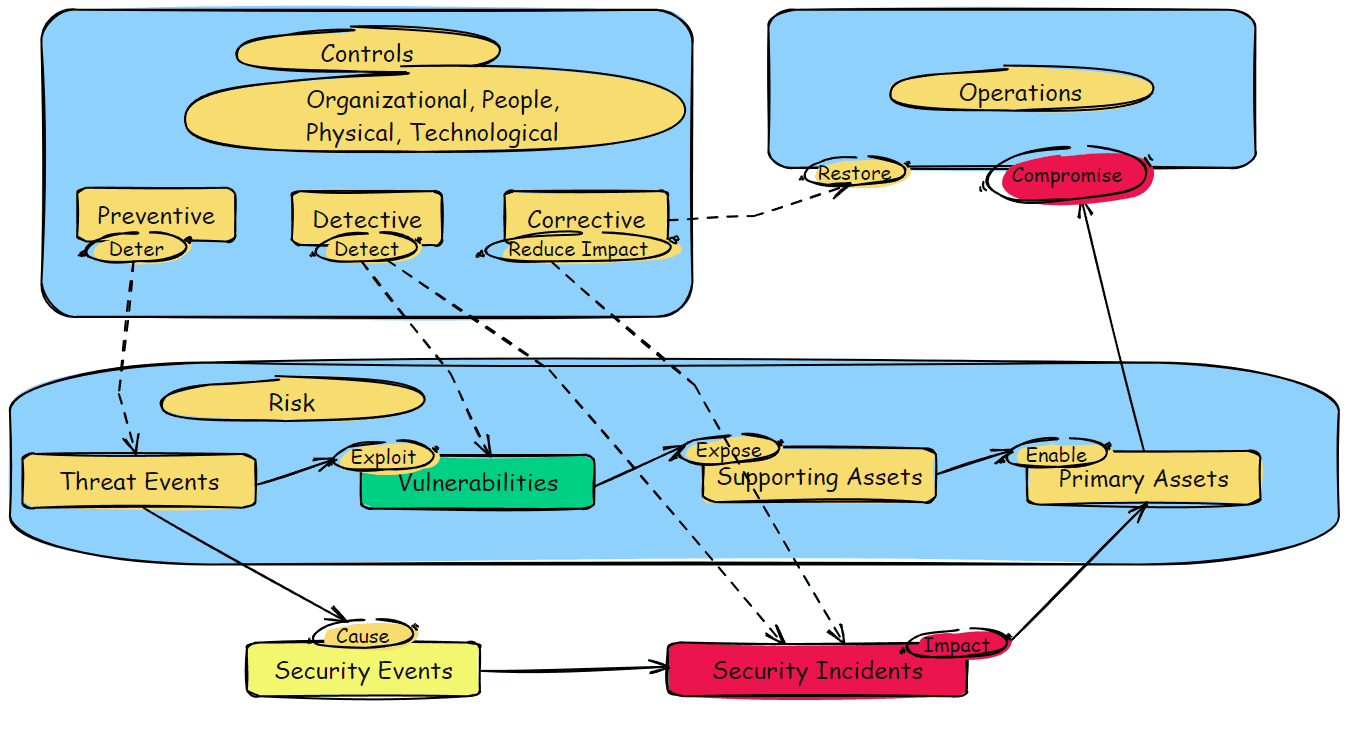
Implementing Controls Through Risk Treatment:
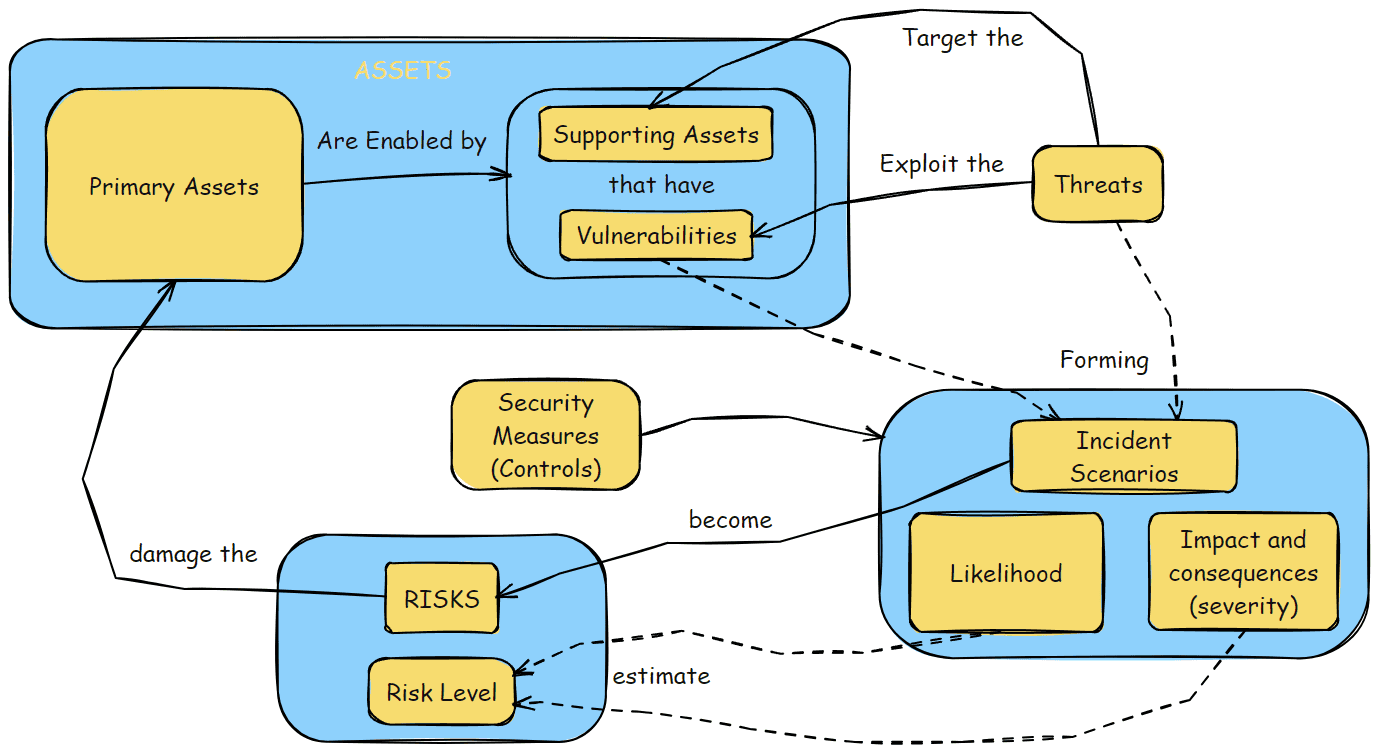
Adding incident scenarios, likelihood and risk levels
A risk assessment scenario brings together three components:
- Threat - What could happen that would lead to a negative outcome?
- Vulnerability - What weakness or opening exists that the threat could exploit?
- Impact - What would be the resulting harm or consequence if the threat exploited the vulnerability?
The scenario describes the full chain of events that could unfold, from the triggering threat, through the exploited vulnerability, to the realized impact or consequence. Analyzing these scenarios helps organizations understand and prioritize their risks.
Risk formulas
Risk = f (Probability, Impact)
Impact or Consequence
Probability or Likelihood
Introducing Threats:
Risk (Threat) = f (Probability (Threat), Impact (Threat))
Introducing Assets:
Risk (Threat, Asset) = f (Probability (Threat), Impact (Threat, Asset))
Introducing vulnerabilities:
Risk (Threat, Asset, Vulnerability) = f (Probability (Threat), Impact (Threat, Asset), Severity (Vulnerability))
Introducing controls:
Risk (Threat, Asset, Control) = f (Probability (Threat), Impact (Threat, Asset), 1-Effectiveness (control))
Risk (Threat, Asset, Control) = f (Probability (Threat, Control), Impact (Threat, Asset, Control))
A lack of control is a vulnerability:
Risk (Threat, Asset, Vulnerability) = f (Probability (Threat, Vulnerability), Impact (Threat, Asset, Vulnerability))
